Network Operations Center (NOCs) Explained
A network operations center (NOC) is a centralized site where IT workers can constantly monitor a network's performance and health. The network operations center (NOC) is the first line of defense against network failures and disruptions.
Organizations receive complete insight into their network through the NOC (pronounced "knock"), allowing them to spot abnormalities and either avoid problems or swiftly remedy them when they arise. The NOC is in charge of infrastructure and equipment (including wiring and servers), wireless systems, databases, firewalls, different network devices (including IoT devices and smartphones), telephony, dashboards, and reporting. Its management solutions also include monitoring customer service calls and the help desk ticketing systems, as well as interaction with customers' network tools, implying that the NOC plays a very important role in providing a great experience to the users.
NOCs can be created in-house and situated on-premise, generally within the data center, or they can be outsourced to a business that specializes in network and infrastructure management and monitoring. Regardless of the architecture, NOC personnel are responsible for identifying problems and making timely judgments on how to remedy them.
NOC - An Overview
What is the function of a NOC?
Simply said, the goal of any NOC is to ensure great network performance and availability while providing continuous uptime. The NOC oversees a wide range of important tasks, including:
- Monitoring the network for issues that require immediate attention, including those that originate from external sources.
- Management of servers, networks, and devices, including software installation, upgrades, troubleshooting, and dissemination across all devices.
- Incident response, which includes handling power outages and communication line problems.
- In addition to security operations, security including monitoring, threat analysis, and tool deployment is also provided.
- Recovery aid from Disasters; data backup and storage (physical and cloud)
- Data management for email, audio, and video.
- Patch management.
- Management of security firewall and prevention intrusion into systems, as well as antivirus assistance
- Policy enforcing.
- Service enhancement through feedback collection and user requests/recommendations.
- Follow through on service-level agreements.
- Management of vendors, freelancers, and contractors.
Network administration, monitoring, and control have never been more difficult to handle. Organizations nowadays are dealing with more complicated networks, with headquarters all over the world, people working from home, and an ever-increasing number of devices to manage and monitor.
The number of users, website traffic, and malware may all influence network speed, thus problems can arise from practically any place. Even seemingly minor difficulties can cause downtime, wreaking havoc on production and your capacity to satisfy the demands of your users/customers.
Gartner published a research article [https://blogs.gartner.com/andrew-lerner/2014/07/16/the-cost-of-downtime/] a few years ago stating that one minute of power/network outage may cost a company $5,600. Network failures reduce revenue, decrease productivity, and ruin the reputation of your IT staff as well as the greater corporation. With this in mind, NOCs are specially built to avoid downtime, so that customers and internal end users are unaware when inevitable faults or outages occur.
What are the primary responsibilities of the NOC?
There will be a team of technicians – NOC engineers, analysts, and operators — as well as multiple team leaders or shift supervisors within the NOC. NOC personnel must possess certain skill sets for monitoring, maintaining, and promptly addressing network performance issues. That kind of expertise is usually beyond the capabilities of the average IT specialist. NOC technicians often have extensive professional experience, particularly in handling network monitoring and tools.
Because a big staff dedicated only to network performance is impractical for many smaller firms, third-party service providers provide NOC services as a substitute for in-house NOCs.
Designing a NOC
An optimal design will provide the NOC with its own dedicated space. One wall might be covered in television screens, each of which displays a real-time view of overall network performance as well as active issues and alerts. The video screens are arranged in a grid and linked together so that they can function as a single huge, high-resolution unit. The physical NOC area and team size are determined by the size of the organization and data center.
Alerts will initially display on the video wall, explicitly telling technicians where a problem is occurring, and which device or line is affected. The television panels may also display news and weather information, allowing personnel to plan around ongoing difficulties that may impact overall network operations. The video wall is also linked to various workstations scattered across the room, where personnel is tasked with monitoring a certain technology or pain point. Technicians can then dig down on related issues and follow methods created to remedy the situation.
Each workstation has many displays, allowing technicians to examine the information and respond more quickly and efficiently. Each station is also linked to a type of PA system, allowing technicians to speak with one another and share information in real-time. Technicians can also display alarm information on the video wall screen for anyone to see.
A separate area devoted to a staff that manages significant network events is common in large businesses.
A NOC will typically hierarchically manage incidents. Technicians are often classified as Level 1, 2, or 3 based on their competence and experience in fixing specific situations. When a NOC technician detects a problem, he or she will produce a ticket that categorizes the problem based on the alert type and severity, among other factors. If the NOC technician assigned to a certain problem level does not handle it quickly enough, the problem escalates to the next level and continues to escalate until the continuing issue is entirely remedied.
The combination of sophisticated technology and highly competent personnel operating under strict standards allows the NOC to function continuously.
What's the boundary between a NOC and a SOC?
While the NOC focuses on network performance and availability, a security operations center (SOC) is made up of tools and staff that monitor, detect, and evaluate an organization's security health 365 days a year and 24 hours per day.
Technicians at the NOC look for faults that might slow down network speed and availability, whereas technicians in the SOC are responsible for identifying cybersecurity risks and responding to assaults. The SOC is concerned with the security of consumer data as well as intellectual property. NOCs often deal with routine and unanticipated network events, but SOCs virtually always respond to external threats attacking the company network.
Both the NOC and the SOC provide vital services to the company, namely identifying, investigating, and resolving issues, and both works to fix issues as rapidly as possible before they harm the business. Furthermore, both often use a hierarchical approach to incident resolution. They do, however, address quite distinct challenges. As a result, employees in both groups have diverse abilities, knowledge, and methods. A NOC technician must comprehend network and application monitoring and administration, whereas a SOC analyst will concentrate solely on security.
However, SOCs and NOCs should work together to address serious issues and during emergencies, therefore the two teams should not be separated. According to SANS research, over a third of firms report little to no interaction between the NOC and SOC, while another 20% believe the teams only work together during emergencies. However, experts advocate for improved NOC/SOC integration. Integrating the two — even if they stay mostly distinct in practice — begins with creating operational rules, automating processes, and implementing technologies that allow for the collection and sharing of network monitoring data across both the NOC and SOC.
Is it possible for a NOC to deliver SOC functionality?
While establishing a separate NOC and SOC is not practical, a NOC can monitor and handle security concerns, however, it is not ideal. NOCs can and do detect security risks affecting network performance, and skilled personnel can respond to them successfully. The latter aspect, though, is crucial. Technicians must be on the lookout for security hazards and be prepared to respond to them. It is difficult to find technicians that are highly knowledgeable in both network performance and security.
In addition to the appropriate skill set, the security-oriented NOC would require specific technologies for security and issue resolution. A fundamental tool, for example, is a security information and event management (SIEM) system, which is a single security management system that provides a comprehensive insight into network activities. SIEM systems gather, process, and categorize machine data from a variety of network sources and analyze the data so that you can respond in real-time. In summary, SIEM automates a large portion of the job of a typical SOC team. This raises the visibility of events while decreasing false positives, making it much easier for a properly staffed NOC to monitor security.
Starting Over
What are the best NOC practices?
A network operations center's best practices focus on training, rely on well-defined responsibilities, and provide explicit protocols and better means of secure communication.
1. Prioritize training and focus on knowledge.
Your NOC personnel must have extensive experience in monitoring, managing, and resolving network performance and IT infrastructure issues. Keep up with the evolving tech world and changes to your IT system by providing thorough and regular training on processes and standards for every event. Prioritize network performance concerns, but don't forget security collaboration protocols with your SOC. Escalation is a critical procedural concern; ensure that your staff understands how and when to make the hard choice to escalate a growing problem to a more experienced teammate.
2. Define separate roles
Flat organizational structures are becoming increasingly prevalent. In the fast-paced, must-act-now environment of network monitoring, it makes more sense to empower each team member than insist on strictly imposed role-based handoffs. While technicians should have the skills and power to respond swiftly to avoid network outages, escalation levels, and shift supervisors are still required to manage the NOC.
While NOC technicians should be left to do their jobs and provide insight largely on their own — and certainly not micromanaged — you need a manager who assigns work to technicians based on their skills, prioritizes tasks, prepares reports, ensures incidents are resolved properly, and notifies the broader organization of events as needed. Furthermore, each technician should be aware of the responsibilities that will be assigned to them, their level, and the line of reporting if they need to escalate or respond to an event.
3. Allow for effective communication.
It can be difficult to keep lines of communication open between the NOC, SOC, and other external teams. It's more than merely scheduling a few meetings regularly. Instead, a significant effort is required to instruct personnel on how and when to disclose information, as well as to hold them accountable for doing so. A solid NOC relies on regular chances for collaboration and coordination.
Create specific norms and protocols: Maintain order by establishing clear policies for the following:
- Incident management: Document the procedures that technicians should use to handle incidents (e.g., when the technician can make the decision when to escalate the decision, when to notify team members, and so on).
- Solutions: Outline techniques for coping with frequent problems and give rapid solutions to crises.
- Escalation: Determine how and to whom the team should escalate concerns.
- Prioritization: Determine which issues are the most essential and which technician level should address them. Incidents should be prioritized depending on their impact on the business.
Having well-defined protocols ensures that everyone is on the same page, offers consistency across the enterprise, and enhances responsibility among NOC personnel. Having the appropriate people and processes in place is important, but the real job cannot be done without the correct tools.
How do you select the best tools for your NOC?
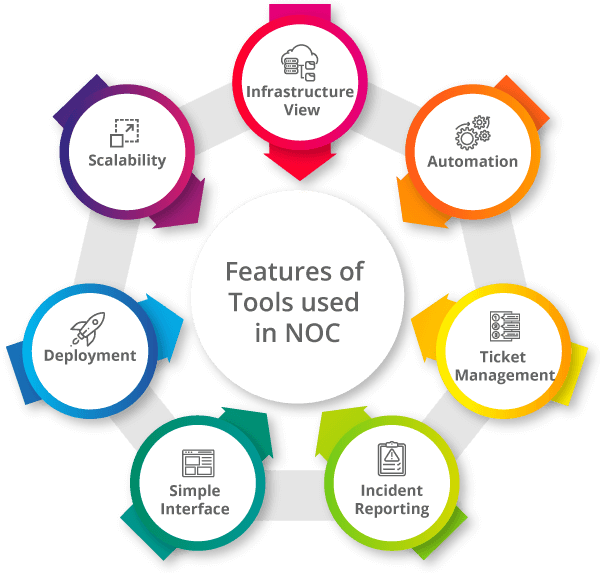
The tool you choose is mostly determined by your business requirements, however, your NOC needs a tool or collection of tools that deliver the following:
- A complete view of your infrastructure: Whether it is physical, virtual, or cloud-based.
- Automation: To reduce the number of repetitive activities, allowing Level 1 employees to focus on higher-priority issues and lowering alert fatigue.
- Ticket management: You may access information about open tickets, such as the priority job and the assigned technician, to guarantee that internal and external issues are resolved swiftly.
- Incident reporting: Using a technology that enables visual analysis, and graphical representations of thresholds, alerts, indicators, and trends, it is simpler to analyze and document concerns.
- A simple interface and deployment: You want to see results right away and not have to deal with a lengthy, difficult deployment and a steep learning curve.
- Scalability: As your company expands, you want to be sure the NOC can keep up.
The tool you use should provide you with comprehensive visibility throughout your whole network, allowing you to drill down further, examine issues, and enhance your overall incident response over time.
NOC for yourself
One of the most significant functional teams in IT is the network operations center. You have internal and external clients that rely on your IT services every day. You must satisfy SLAs (service level agreements), support fundamental business efficiency, and sustain your clients' whole digital experience.
It is critical to have a NOC capable of averting catastrophic failures and maximizing the availability of all IT services. Many businesses have a NOC, but it may be difficult to keep it fully staffed, appropriately educated, and well-equipped with the most up-to-date technologies and automation. Organizations that are unable to maintain an efficient NOC may find third-party service vendors, often known as managed service providers, to be more effective.
The Proinf platform bridges the gap between data and action, enabling observability, IT, and security teams to assure their businesses' security, resilience, and innovation. We provide an open, extensible data platform that enables shared data in any environment, allowing all teams in an organization to have end-to-end visibility, with context, for every interaction and business activity. Proinf can help you establish a solid data foundation.