Transform your cybersecurity posture with the advanced threat hunting strategies
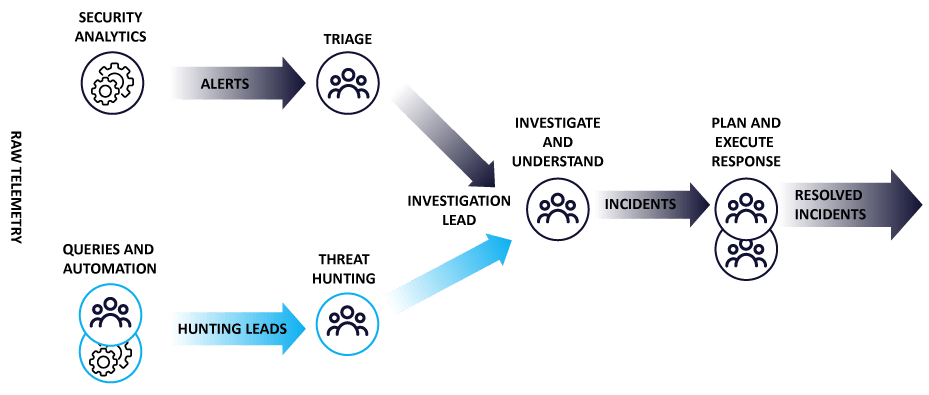
What is Cyber Threat Hunting?
Threat Hunting or Cyber threat Hunting is a proactive approach to identify unknown or ongoing non-remediated threats, within an organization’s network.
It is an active information security strategy used by a security analyst. It consists of searching iteratively through networks to detect Indicators of Compromise – IoC or Indicators of Attack – IoA, hacker tactics, techniques, and procedures – TTP, and threats such as Advanced Persistent Threats – APTs that are evading existing security systems.
Cyber Threat Hunting Activities Include:
1. Hunting for insider threats or outside threats or attackers:
Cyber threat hunters can detect threats posed by insiders like employees and outsiders like criminal organizations.
2. Actively looking for known adversaries:
A known attacker is someone whose code pattern is on the deny list of known dangerous programs or who is identified in threat intelligence services.
3. To find hidden risks and stop an assault from happening:
Threat hunters constantly watch the computer environment and can identify irregularities that might point to a threat through behavioural analysis.
4. Predict & Update Response Plan:
Threat hunters evaluate a threat as thoroughly as they can before implementing the incident response strategy to counter it. This is used to update the response plan and prevent any similar attacks.
Types of Cyber Threat Hunting:
1. Structured Threat Hunting:
Structured Threat Hunting is based on the IoA (Indicators of Attack), and TTP (Tactics, Techniques, and Procedures), of an attacker. All hunts are coordinated and dependent on the threat actors' TTP. So, the hunter can identify the threat actor before the attacker can damage the environment. This hunting type uses the MITRE ATT&CK framework using PRE-ATT&CK and enterprise frameworks.
2. Unstructured Threat Hunting:
Unstructured Threat Hunting is initiated based on the trigger which is considered one of the IoCs. Threat Hunters often looks for pre- and post-detection patterns. In guiding their approach, the hunter can research the data retention and previously associated offenses.
3. Situational or Entity-Driven Threat Hunting:
A situational hypothesis comes from an enterprise’s internal risk assessment or the trends and vulnerabilities analysis unique to the IT environment.
Entity-oriented leads come from crowd-sourced attack data that when reviewed can reveal the latest TTP of current cyber threats. A threat hunter can search for these specific behaviour patterns within the environment.
Cyber Threat Hunting Models or Methodologies:
1. Intelligence or Intel-based Threat Hunting:
Intel-based threat hunting is a reactive threat-hunting model using IoCs from intelligence sources. The hunt follows predestined rules set by the SIEM and threat intelligence. Intel-based hunts can use IoCs, hash values, IP addresses, domain names, networks, or host artifacts provided by intelligence-sharing platforms such as Computer Emergency Response Team – CERT. These platforms allow for the export of automated alerts in the form of Trusted Automated Exchange of Intelligence Information (TAXII) and Structured Threat Information Expression (STIX), which can then be imported into SIEM. Once the SIEM has issued the warning based on an IoC, the threat hunter can look into the harmful activity that occurred before and after the alert to discover any environmental breach.
2. Hypothesis-based Threat Hunting:
Hypothesis-based threat hunting is a proactive threat-hunting model that uses a threat-hunting library It’s aligned with the MITRE ATT&CK framework and uses the global detection playbooks to identify APT groups and malware attacks.
Hypothesis-based hunts use IoAs and TTP of attackers. Depending on the environment, domain, and threat behaviour patterns utilized to form a hypothesis in line with the MITRE ATT&CK paradigm, the hunter determines the threat actors. Once the behaviour pattern is identified, the hunter monitors the activity patterns to detect, identify and isolate the threat. As such, the hunter can proactively detect the threat actors before they can damage the environment.
3. Custom Threat Hunting or Hybrid Threat Hunting:
Custom threat hunting is based on situational awareness and industry-based hunting methodologies. It detects anomalies in SIEM and EDR tools and may be tailored to meet the needs of the customer. They are proactively executed based on situations, such as geographical issues and targeted attacks. Both Intel and hypothesis-based hunting models employing IoA and IoC information can be used in these hunting operations.
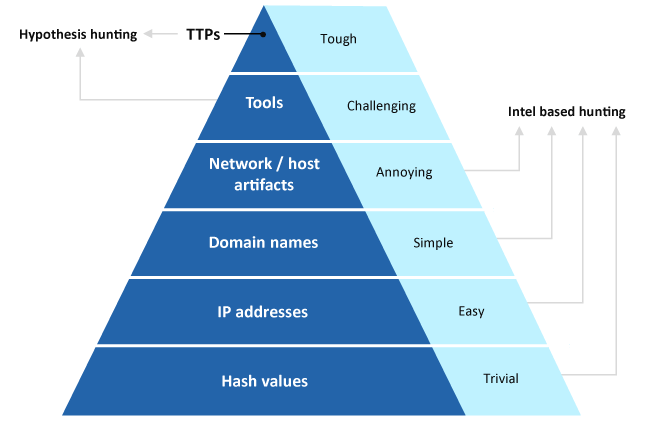
Fig: David Bianco’s Pyramid of Pain
Steps in Threat Hunting:
1. Trigger:
When sophisticated monitoring technologies see unexpected activities that could be indicative of malicious activity, a trigger directs threat hunters to a particular application/system or region of the network for further study. A newfound danger assumption is frequently the catalyst for proactive hunting. Threat hunter collects information about the environment and raises hypotheses about potential threats and then chooses a trigger for further investigation.
2. Investigation:
In the investigation stage, threat hunters delve deeply into any suspected malicious breach of a system using technologies like EDR. Until the activity is determined to be benign or a clear picture of the harmful behaviour is developed, the inquiry will continue.
After selecting a trigger, the hunter concentrates their efforts on actively looking for deviations that either support or refute the theory. In this phase, threat hunters employ a variety of techniques to help them look into abnormalities that could or might be harmful.
3. Resolution:
The resolution phase involves the communication of relevant malicious activity intelligence to operations and security teams so that they can respond to the incident and mitigate the threats. It is possible to feed automated technology with information regarding both harmful and beneficial activities to increase its efficiency without further human involvement.
Information collected during the above phases is communicated to other teams and tools that can respond, prioritize, analyse, or store the information for future use. Whether the information is benign or malicious activity, it can be used in future analysis and investigation. It can be used to predict future trends, prioritize, and remediate vulnerabilities, and improve security measures.
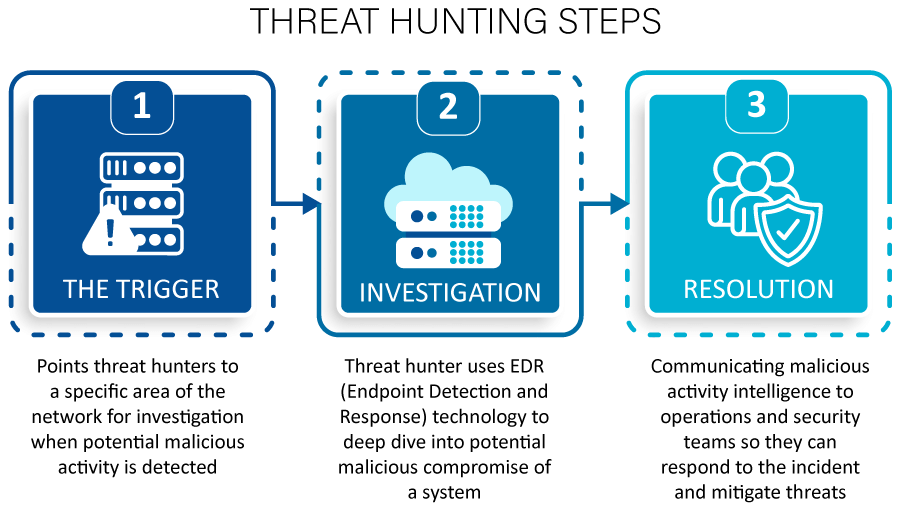
Fig: Threat Hunting Steps
Threat Hunting Frameworks
There is a no. of threat-hunting frameworks which organizations can employ. Two of the most popular are:
1. TaHiTI – Targeted Hunting integrating Threat Intelligence framework
This framework is aligned with intel-based hunting. Threat intelligence, past occurrences, red teaming efforts, and other sources are sources of triggers.
2. MITRE PRE-ATT&CK and ATT&CK frameworks
These frameworks offer the expertise that may be used to address certain threat models and adversarial tactics.
An effective defence against threat actors is provided by a threat-hunting team's use of combinations of these techniques and resources as necessary.
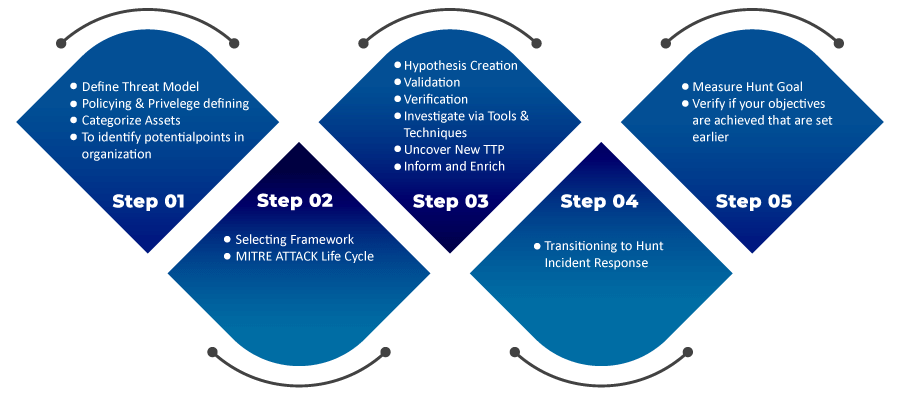
Threat Hunting Process:
The actual threat hunt process starts from Step 3 in the above figure. Pre-hunt activities are integrated into our approach.
The threat-hunting is a cyclic process by nature. It consists of four processes.
- Creation of a hypothesis.
- Verifying and validating the hypothesis. This process also includes further investigation for any proof with the help of Tools and Techniques.
- Uncover new TTP and patterns.
- Inform and Enrichment. It is informing the incident response team about new TTP's which updates new threat definitions and categorizes threats using YARA and STIX.